Alongside illegal data mining other types of information security incidents are common to the public such as denial of service attacks DOS DDOS defacement malware phishing spam and unauthorized access. -Malicious links -Phishing scams -Strong password -Webmail policies What are some non-technical physical steps you can take to being a great human firewall.
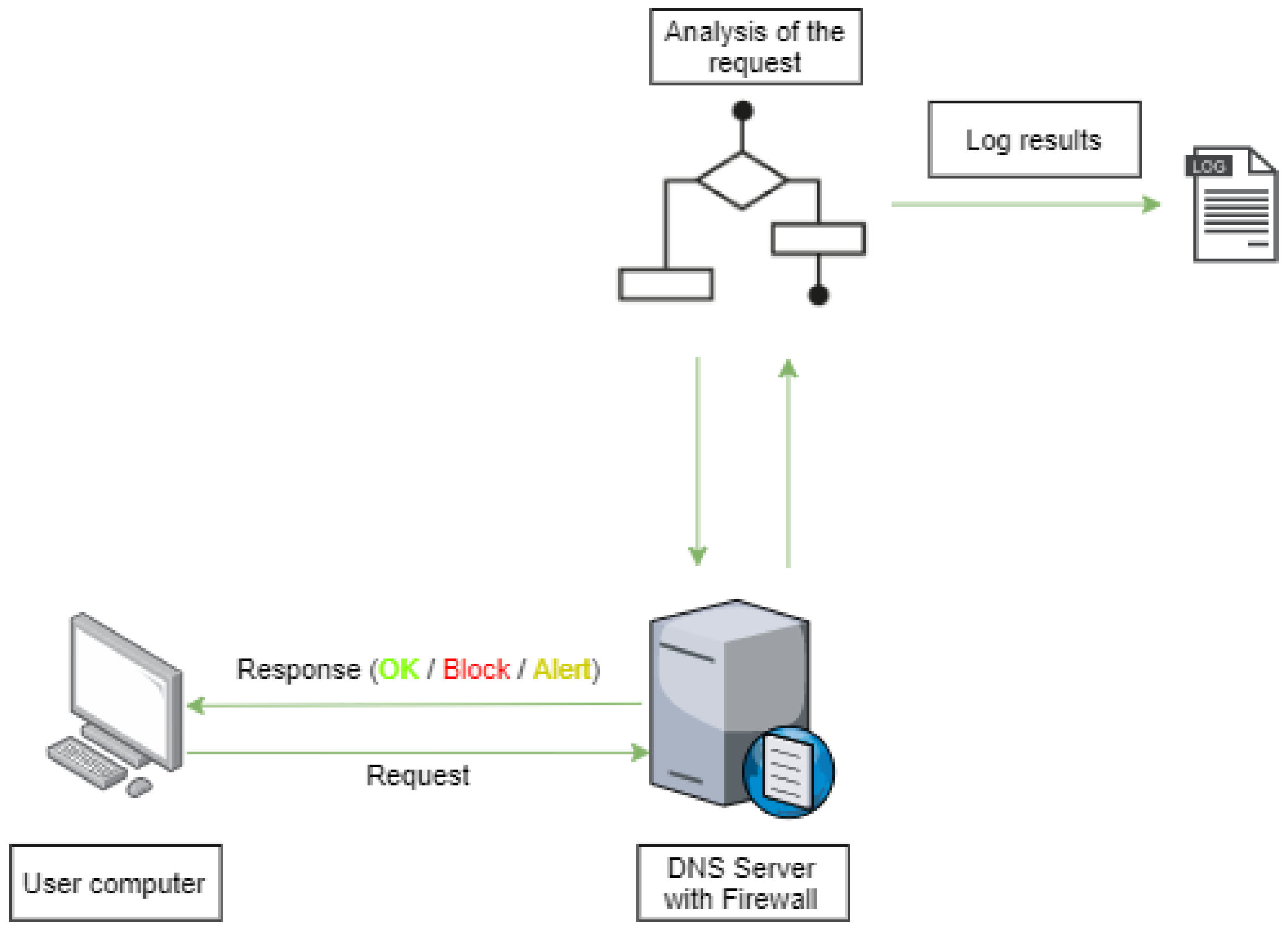
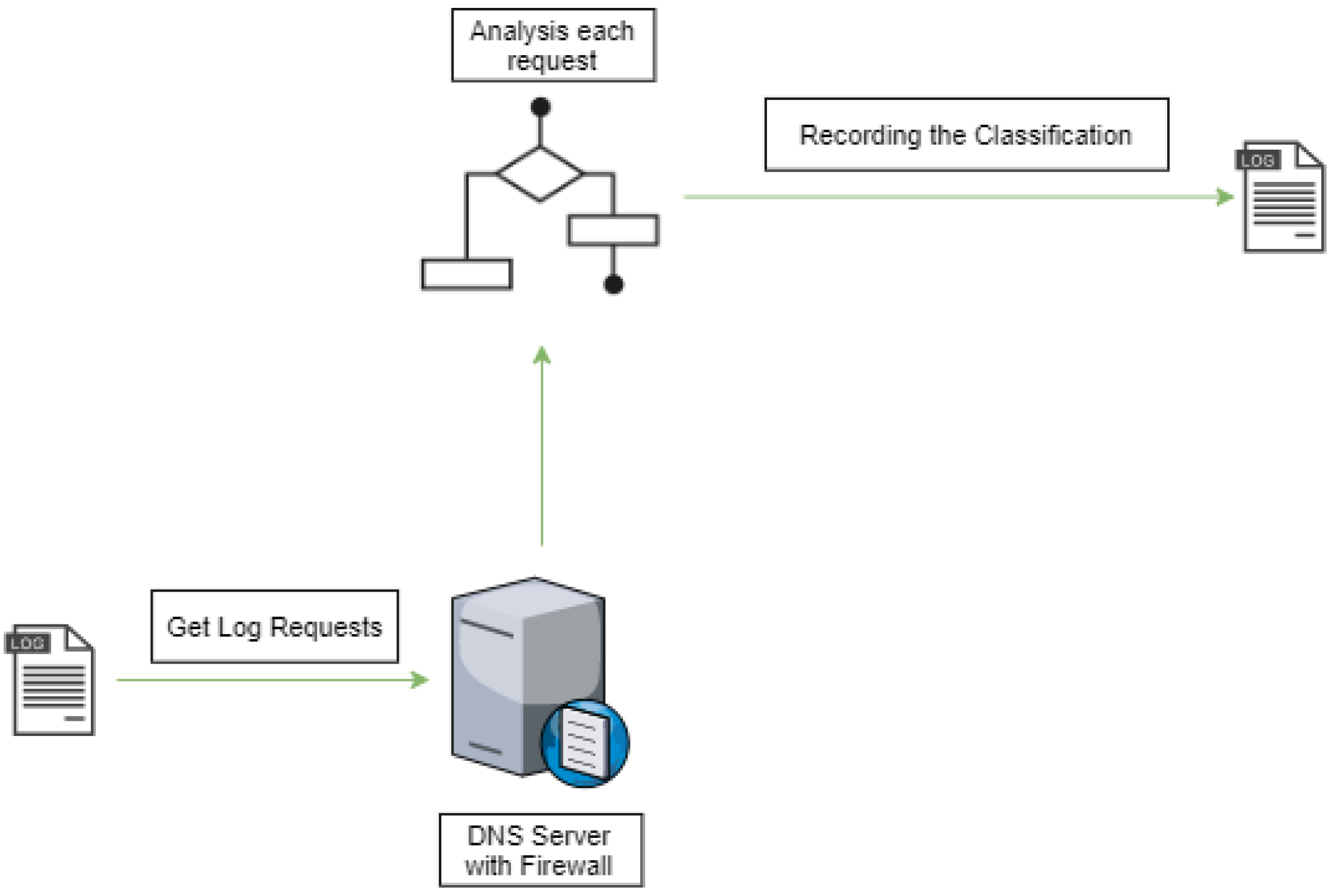
Future Internet Free Full Text Dns Firewall Based On Machine Learning Html
People Physical Cyber Which of these things is part.
. Select 4 Phishing emails Malicious links Clean Desk The Insider Badges Strong passwords Lost Thumb Drives webmail policies 3. What are the three security domains human firewall. The best protection Last year was a year of blackmail viruses and all indications are that this type of threat has reached its.
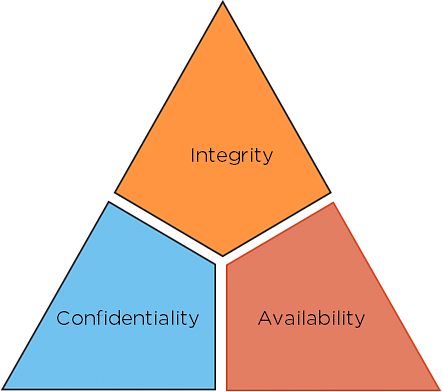
View firewall quiz1001docx from COMPUTER 123 at Southern New Hampshire University. Confidentiality keeping secrets secret Integrity ensuring information is not modified and Availability keeping electronic doors open and IT shops humming. What is a cyber domain.
Malware often appears as popups on a website or browser you are using. Confidentiality integrity and availability CIA. The InfoSec Institute identifies 7 elements required for a successful human firewall approach.
Shore Up Your First Line of Defense. The CIA Triad below outlines these three tenets. People Physical Cyber 1 What are the three security domains.
Make adoption easier by strengthening a few weaknesses at a time. Security awareness individual behavior and actions are key areas of strong and healthy human firewall. According to the latest figures from the Ponemon Institute the average cost of a data breach has reached nearly 65 million in the US alone.
The CIA Triad below outlines these three tenets. Active practice asking the audience to apply the concepts instead of passively receiving the information. Wed 10 Aug 2016.
Human Firewall Image. What are the three security domains. Beside above what 4 things are part of the cyber domain.
Strengthening Email Security where I was joined by Mimecast Product Manager Steve Malone and Forrester Research Analyst Nick Hayes. Malware The chance of downloading malware to your computer in the course of carrying out everyday work tasks is relatively high. The three primary tenets for information security governance and risk management are.
Divided cybersecurity into four domains. The Security Domains Triad. Right now most organizations arent doing an.
Make it easy Dont overwhelm people with too much information at once. -Cyber -Physical -Human or People Which of these things is part of the CYBER domain. A human firewall is always aware of phone scams and is aware of which data to avoid sharing over the phone.
Three Key Elements for Building an Effective Human Firewall. What are the 3 security domains. Which of these things is part of the CYBER domain.
Availability People Physical Integrity Confidentiality Cyber 2. To explore the problem further last week I hosted a webinar The Human Firewall. 317 views Erik Fair Studied Computer Science Economics at University of California Berkeley Graduated 1983 Upvoted by Tony Li.
Your human firewall encompasses how well employees understand the importance of the right security practices and how easily they can act on them. Availability People Physical Integrity Confidentiality Cyber 2. First you must bring all the employees at your Company onboard with the ways to protect the Companys security system.
Here are three takeaways from the webinar. Thus this domain focuses on the design and architecture of the network and its components to prevent the disruption of data flow and intrusion. Spaced retrieval fast learning leads to fast forgetting while long-term retention results from information being retrieved regularly over a period of months to strengthen the pathways to permanent retention.
And it is not only an organization or any Government but each and every individual who is responsible for all types of securities. We recently discussed the tried-and-true CIA information securitytriad. Keep education ongoing Ad hoc or a few times a year is simple not enough for such an evolving threat landscape.
Confidentiality Network security protocols Network authentication services Data encryption services Integrity Firewall services Communications security management. S3 -Keeping your desk clean organized. Make it easy Dont overwhelm people with too much information at once.
Cyber attacks arent just getting more frequent they are also becoming significantly more vicious and sophisticated. The key components of this domain are. Stay safe and act as a strong human firewall safeguarding the designated assets in this hi-tech world.

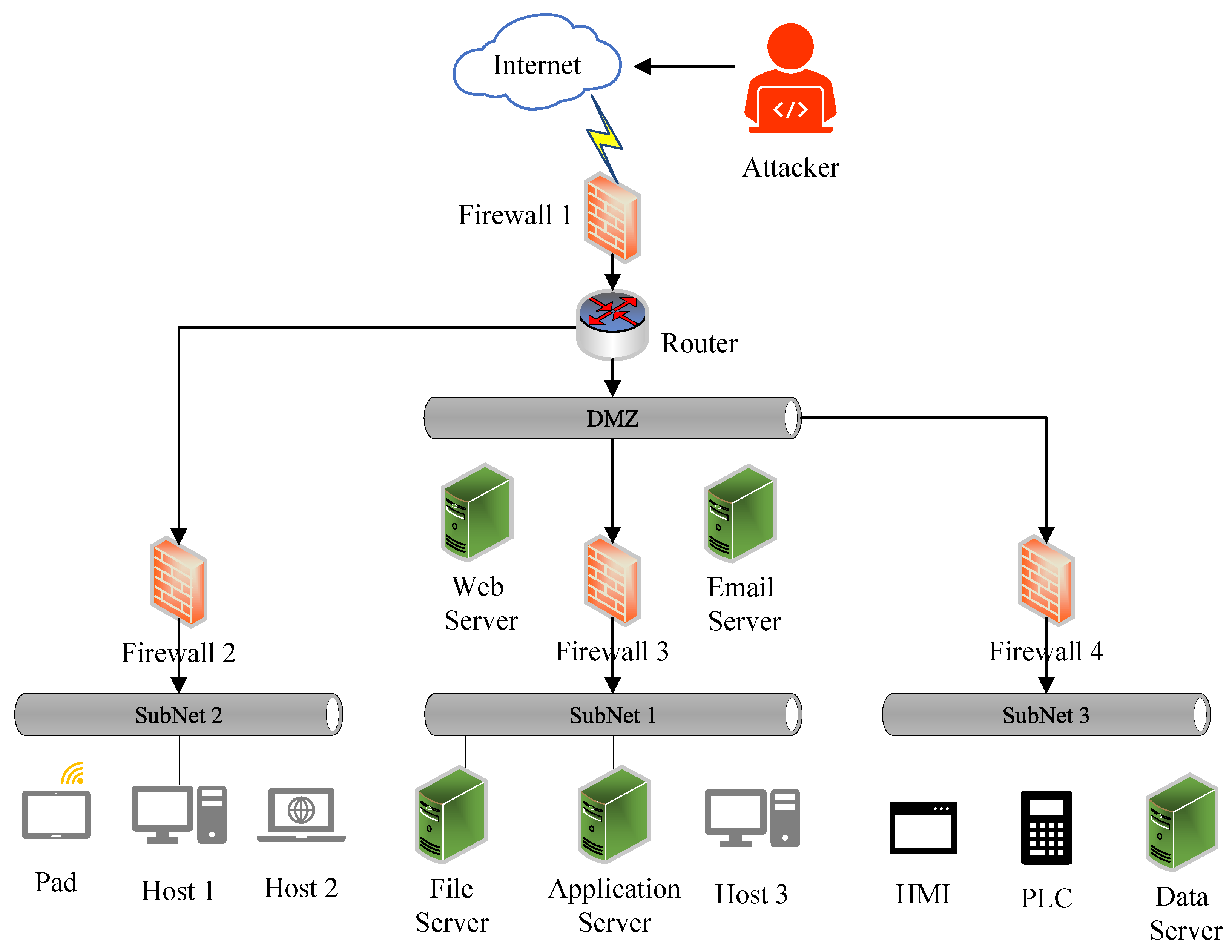
Applied Sciences Free Full Text Attack Categorisation For Iot Applications In Critical Infrastructures A Survey Html

Electronics Free Full Text Recent Progress Of Using Knowledge Graph For Cybersecurity Html

Future Internet Free Full Text Dns Firewall Based On Machine Learning Html
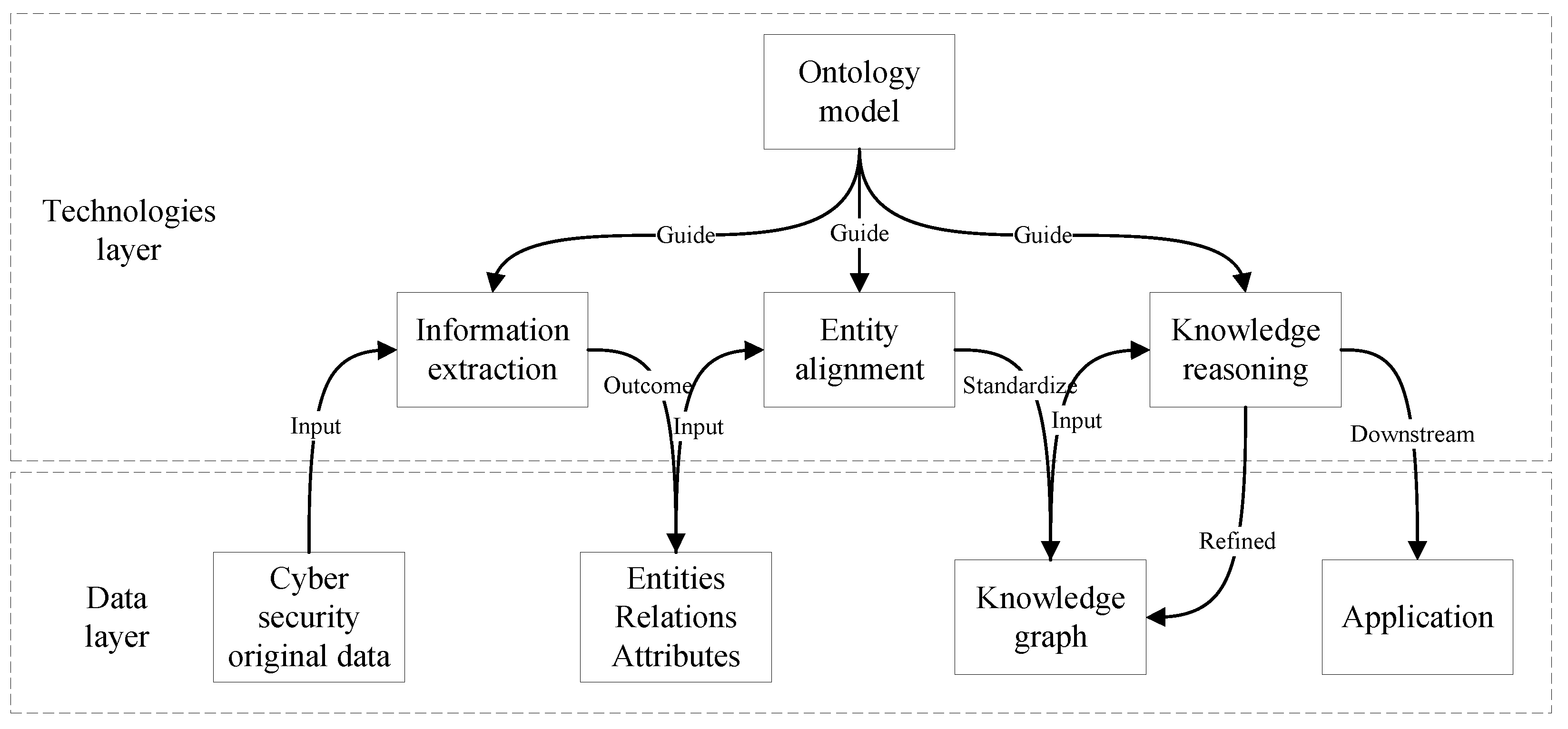
Electronics Free Full Text Recent Progress Of Using Knowledge Graph For Cybersecurity Html
Electronics Free Full Text Recent Progress Of Using Knowledge Graph For Cybersecurity Html
What Is Cybersecurity Importance Of Cyber Security Simplilearn

What Is Cybersecurity Importance Of Cyber Security Simplilearn

0 comments
Post a Comment